
Recent reports from multiple sources reveal the weight of ransomware attacks has recently skewed towards MSP networks.
Sources confirm in some cases the hacker’s penetration causes disabling backup and disaster recovery (BDR) systems.
Depending on how MSP’s handle end-customer separation from MSP environment – the ransomware can either be propagated to the end-customer fleet or it can be contracted from end-customer environment and travel across MSP network.
On the top of commonly suggested steps to prevent ransomware attacks or to reduce their consequences ActiveImage Protector offers a few features, some of them are unique:
1. ActiveVisor – ActiveImage Protector site managing suite – can alert about an absence of backups against a defined threshold
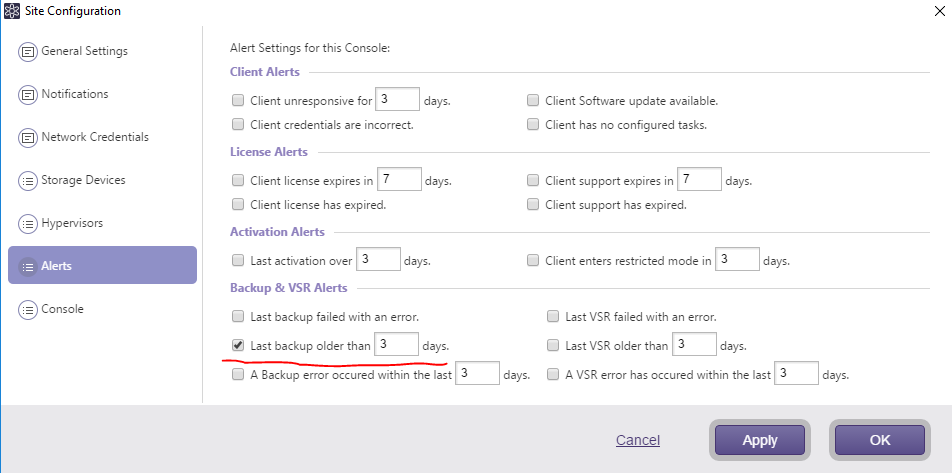
This type of alert is preferred since the backup schedules can be altered silently, disabling normal “success/failure” routine.
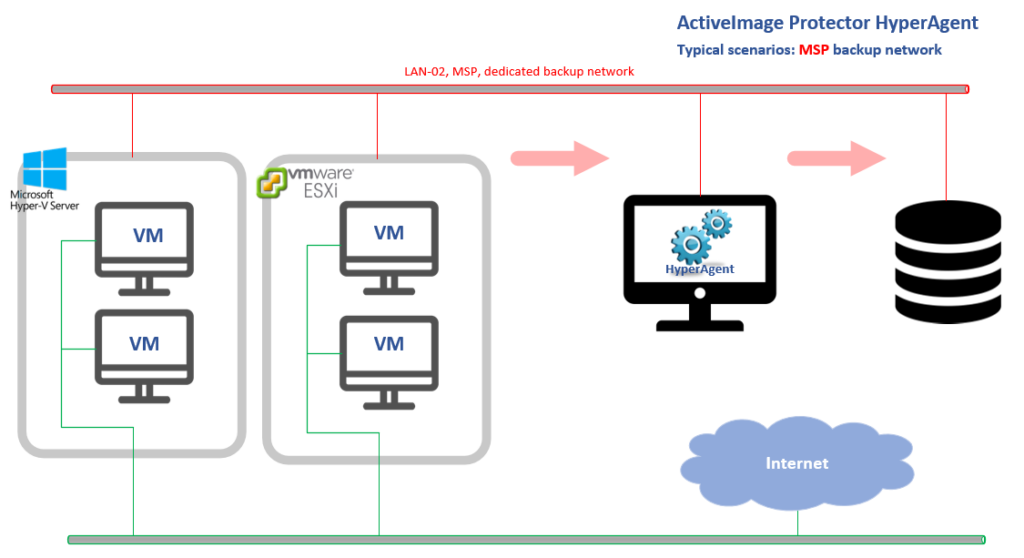
2. ActiveImage Protector HyperAgent – crucial component of ActiveImage Protector Virtual Edition – allows full separation between MSP and end-customer environments.
ActiveImage Protector HyperAgent component is designed to backup virtual machines from outside, i.e. in “agentless” fashion on hypervisor level, so the end-customer’s environment might have no visible or sensible traces of ActiveImage.
Moreover the end-customer’s space can/will be completely isolated from MSP, even on a network level since ActiveImage Protector HyperAgent is not required to run within end-customer network segment.
3. Finally – ActiveImage Protector offers a unique way to avoid/reduce ransomware damage to backup destinations and their content (i.e. backups themselves). This feature is called “Destination Isolation Options” but is also known as “Anti-Malware options”.
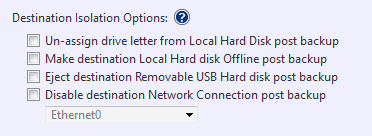
These options are present during a backup configuration and go as following:
- Un-assign drive letter from Local Hard Disk post backup – if backup is pointed to a local disk space, the destination disk’s letter will be unassigned as soon as the backup completes. As a result, the destination disk will not be visible to all other programs and may skip being examined by ransomware as a potential target. ActiveImage Protector automatically reassign the drive letter right before the next scheduled backup attempts and unassigns the letter again after backup is completed.
- Make destination Local Disk Offline post backup – the same as #1 option with one difference, destination disk will be marked as Offline. ActiveImage brings the destination disk Online right before the next scheduled backup attempt and takes it Offline right after backup is completed.
Both above options can be combined or used separately, both are relevant to the cases where destination is an internal disk other than source of backup of course.
- Eject destination Removable USB Hard disk post backup – in case of externally connected USB used as a backup destination the backup will finish with disconnecting this USB drive from the OS. Next scheduled backup attempt to this destination will fail unless the USB drive is reconnected (human interaction will always be required for that). At the surface this option may seem to be harsh and unattractive, however on a scale of anti-malware means this has heavier protection score and has its place in a scope of use cases.
- Disable destination Network Connection post backup – relevant with destination being a network share. Needless to say, a separate (dedicated to backups) NIC has to be allocated with this option. It’s probably common sense to put this NIC on a different from the production subnet. The NIC will be disabled as soon as backup completes. ActiveImage Protector will enable it right before the next scheduled backup attempt and will again disable it right after backup finishes.
All the above listed means by ActiveImageProtector compliment the mainstream cybersecurity suggested steps to protect the MSP/end-customer’s environment from hacking/malware attacks such as:
- Embrace Multi-Factor Authentication – Activate two-factor/multi-factor authentication (2FA/MFA) on all systems — including MSP software platforms, administrator systems and end-user systems wherever possible;
- Configure BDR and Security System Alerts (such as #2, ActiveVisor alert configurations);
- Embrace an MSP Documentation Platform to document your data protection and cybersecurity processes, disaster recovery plans, etc.;
- Stay Informed on security threats;
- Build Your Long-term Plan to mitigate risk;
- Boost MSP Employee and End-user cybersecurity Awareness;
- Integrate vendor Wisely into your cybersecurity plan/layout (for example use the above listed features as part of your actions);
- Partner with MSSPs (Managed CyberSecurity Service Providers);
- Extend to attend major cybersecurity events — particularly RSA Conference, Black Hat and Amazon AWS re:Inforce.



